If you run a website that uses a database, you’ve likely heard the term “SQL Injection” or “SQLi.” It sounds technical and intimidating, but the concept behind this common cyberattack is surprisingly simple. Unfortunately, it’s also one of the most dangerous vulnerabilities a website can have.
Today, we’re going to break down what SQL Injection is, how it works, and most importantly, how you can prevent it, all with easy-to-understand examples.
What is SQL Injection? Imagine a Naive Clerk
Think of your website’s database as a very obedient but literal-minded clerk working in a massive file room. To get information, a user fills out a request form (like a login or search form on your site).
- A Normal Request: A user wants to find their profile, so they type their username,
JohnSmith, into the username field. The form goes to the clerk, who is instructed: “Find the file for the user named ‘JohnSmith’.” The clerk walks to the “J” cabinet, finds John Smith’s file, and hands it over. Everything works as it should. - A Malicious Request (SQLi): Now, imagine a hacker gets the same form. Instead of just a name, they write a tricky, compound instruction like: “Find the user named ” OR 1=1 –“
Because our clerk is programmed to follow instructions exactly, they don’t see this as just a name. They interpret the hidden commands. The instruction tells the clerk: “Find a user whose name is empty… or find a case where 1 is equal to 1.”
Since “1=1” is always true, the clerk becomes confused and is tricked into handing over every single file in the user cabinet, starting with the very first one—which often belongs to the administrator.
This is the essence of an SQL Injection (SQLi) attack. It’s a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. By inserting malicious SQL code into a user input field, the attacker can trick the database into executing unintended commands.
How Does the Attack Actually Work?
Let’s look at the code behind a typical login form. When a user enters their username, the server builds a database query that looks like this:
SELECT * FROM users WHERE username = 'USER_INPUT';
This command tells the database to select all information (*) from the users table where the username column matches what the user typed in.
Scenario 1: A Legitimate Login
- You type your username:
my_username - The database query becomes:
SELECT * FROM users WHERE username = 'my_username'; - The database finds your user record and logs you in. Simple!
Scenario 2: An SQLi Attack
- A hacker types this into the username field:
' OR 1=1 -- - Now, the database query becomes:
SELECT * FROM users WHERE username = '' OR 1=1 --';
This looks like gibberish, but to the database, it’s a set of perfectly valid commands. Let’s dissect the hacker’s input:
'The first single quote immediately closes the text field forusername, leaving it empty.OR 1=1This adds a new condition. The query now asks the database to find a user where the username is empty OR where 1 is equal to 1. Since 1 always equals 1, this condition is universally true.--This is a comment operator in SQL. It tells the database to completely ignore the rest of the query. This is useful for neutralizing any legitimate code that might come after the input, like a password check.
The database evaluates the OR 1=1 condition, finds that it’s true, and returns the data for all users from the table. In many cases, this is enough to log the hacker in as the first user in the database, who is typically the system administrator.
The Dangers: Why SQLi is So Bad
A successful SQL Injection attack is not a minor bug; it can be catastrophic. An attacker can potentially:

- Bypass Authentication: As seen in our example, they can log in as any user, including administrators, without needing a password.
- Steal Sensitive Data: Hackers can “dump” entire database tables, stealing user lists, passwords, personal information, credit card numbers, and other private data.
- Modify or Delete Data: An attacker could change user passwords, delete records, or alter the content on your website.
- Gain Full Control of the Server: In severe cases, an SQLi vulnerability can be leveraged to gain access to the underlying server, giving the attacker complete control over your website and its data.
How to Prevent SQL Injection Attacks
Fortunately, protecting your website from SQLi is straightforward if you follow modern best practices.
1. The Best Defense: Use Parameterized Queries (Prepared Statements)
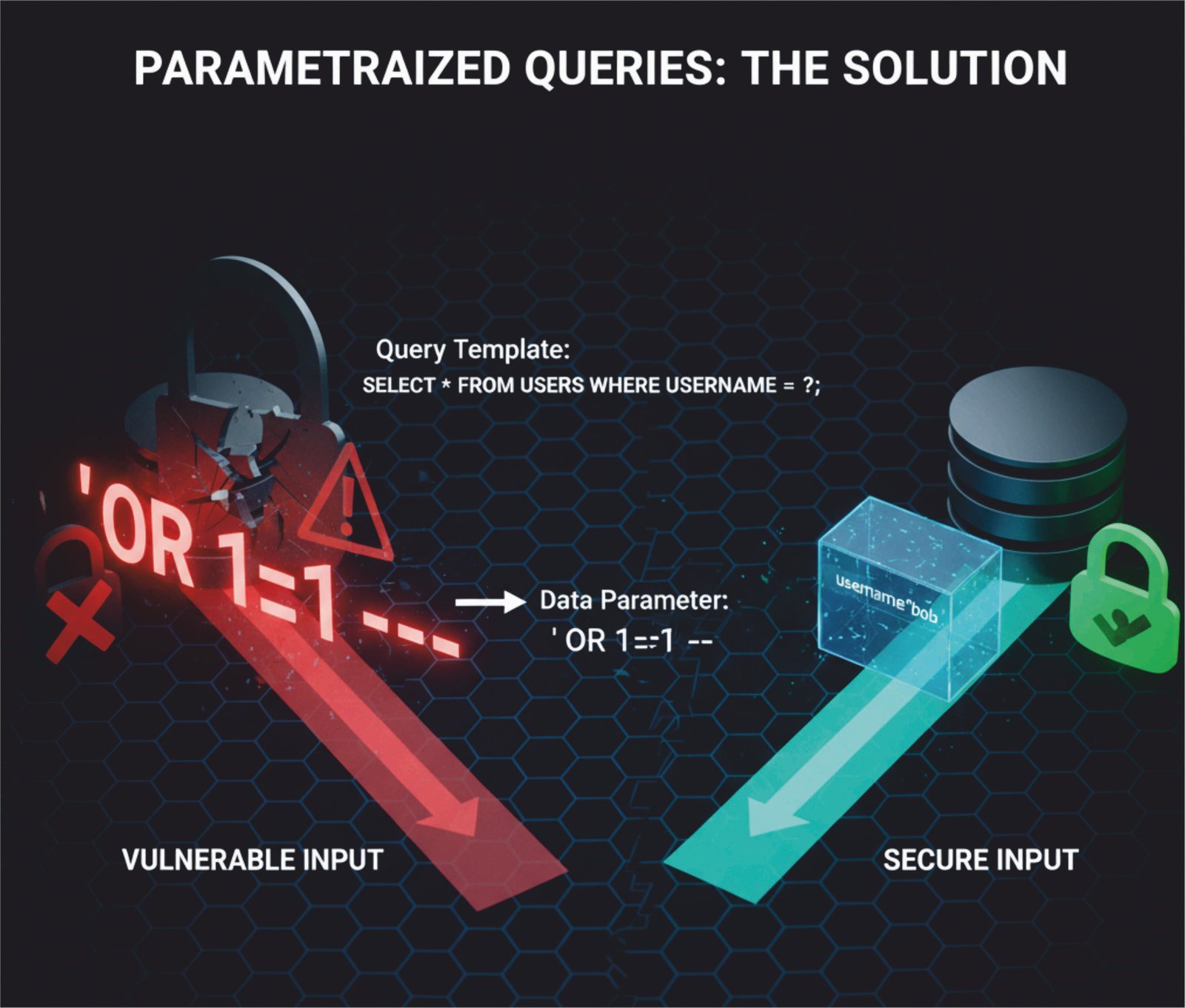
This is the gold standard for preventing SQLi. Let’s go back to our clerk analogy.
Instead of giving the clerk a form where the user can write anything, you give the clerk a strict template with a locked box. The template says: “Fetch the file for the user whose name is in this box.” The user’s input (JohnSmith or the malicious ' OR 1=1 --) goes directly into the box.
The clerk is now instructed to only use the content of the box as a search term. They will never execute it as a command. If a hacker puts ' OR 1=1 -- in the box, the clerk will simply look for a user with that exact, bizarre name. They won’t find one, and the attack fails.
In programming, this is called a parameterized query or a prepared statement. The SQL query is sent to the database first as a template, and the user’s input is sent separately as a parameter. The database uses the parameter only as data, never as a command, making injection impossible.
2. A Good Practice: Sanitize and Validate User Input
While parameterized queries are the best solution, it is also crucial to treat all user input as untrusted. Input sanitization is the process of cleaning up user input by removing potentially dangerous characters like ', ;, and --.
For example, you can implement a function that strips these characters from any data submitted through your forms before it ever touches the database. This adds an extra layer of defense.
Key Takeaways
- SQL Injection (SQLi) is a serious attack where hackers hide malicious commands in user input fields.
- The root cause is trusting user input and mixing it directly with database commands.
- The consequences range from data theft to a complete server takeover.
- The most effective way to prevent it is by using parameterized queries, which keep user data separate from executable commands.
Protecting your website starts with understanding the risks. By implementing secure coding practices, you can shut the door on SQL injection and keep your data—and your users—safe.
For those who want to dive deeper into the technical details and explore code examples for different programming languages, the official OWASP SQL Injection Prevention Cheat Sheet is an essential resource used by security professionals worldwide.
